x对面断点调试案例分析
POST /app/login/signup.app HTTP/2
Host: zc.vjkeji.com
X-Requested-With: XMLHttpRequest
Vs_app_version: 3.0.4
Vs_nonce_str: F12m8iGarppGa2WDOJUO8YayOeV2V0bx
Vs_device_id: 865166029891887
Vs_device_name: redmi note 3
Online_type: android
Vs_timestamp: 1650961572898
Vs_request_fromapp: f2f
Accept: application/json
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Connection: keep-alive
Content-Type: application/json
Cookie: JSESSIONID=F4A316916F1EAC3BE9C7D85AE94C471E; route=f5cf0741684208119280e061e407700e
User-Agent: Mozilla/5.0 (Linux; U; Android 5.1.1; zh-cn; redmi note 3 Build/LMY48Z) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30
Content-Length: 207
{“password”:”057fa5c78d2bb0139a35a65011edc6dd”,”countryCode”:”86”,”sign”:”03e0497b9c2352c7098defc43b3d1a92”,”userName”:”13618396959”,”nonceStr”:”TQbBR5qJO3rImsVJZ72rj5hTYmM6yxG6”,”timestamp”:”1650961572897”}
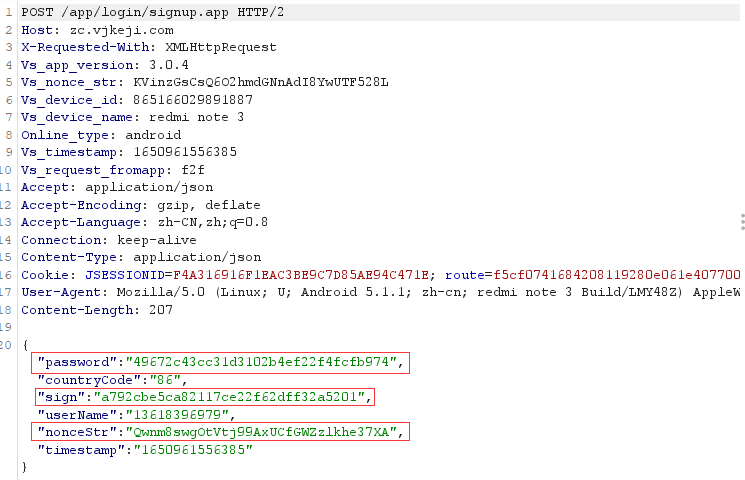
查找nonceStr
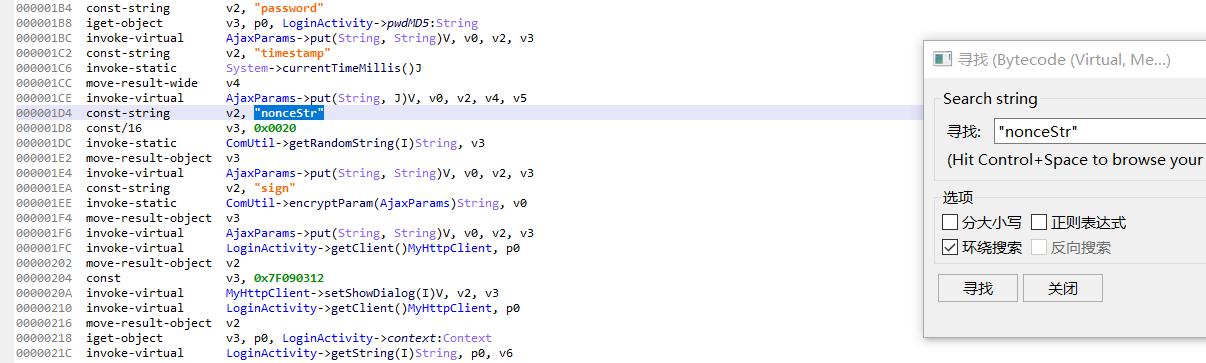
反编译:
要分析的字段:
password
sign
nonceStr
Vs_nonce_str
password
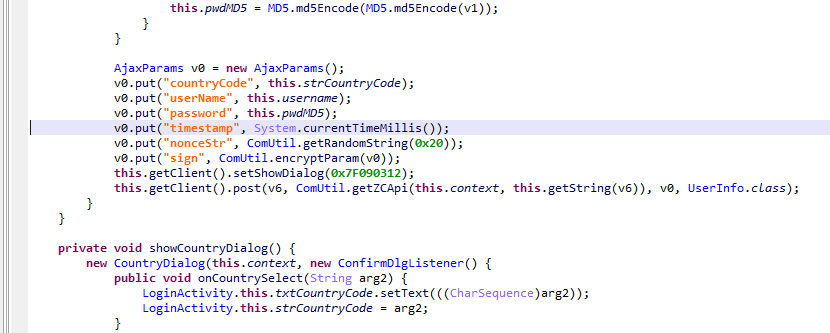
跳转后
因此,大胆判断就只是md5加密
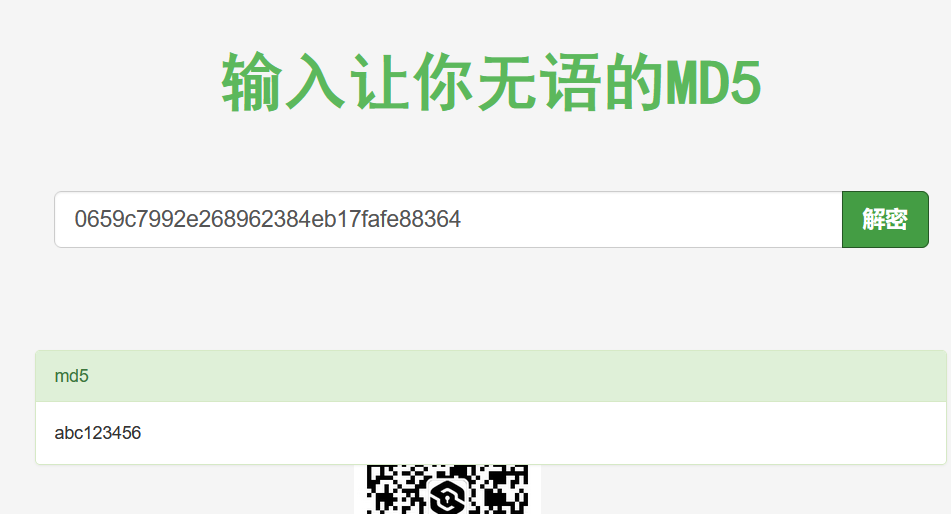
用js工具加密abc123456得到0659c7992e268962384eb17fafe88364
057fa5c78d2bb0139a35a65011edc6dd
不对
用网上的md5解密057fa5c78d2bb0139a35a65011edc6dd得到0659c7992e268962384eb17fafe88364
好了,现在可以看出来是两次md5加密后的值了
sign
03e0497b9c2352c7098defc43b3d1a92
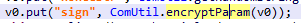
1 | public static String encryptParam(AjaxParams arg2) { |
1 | public static String encryptMap(Map arg11, boolean arg12) { |
arg11 = v0(上边那一堆字符串)
arg12 = false
v4 = countryCode=86&userName=13618396959&password=abc123456×tamp=1650961572897&nonceStr=TQbBR5qJO3rImsVJZ72rj5hTYmM6yxG6
v4+75cba6dd6d4d75154624dbe9d770d451 用md5加密(这里也要看 里面还有填充0和UTF-8) -> a
v2 = a
countryCode=86&userName=13618396959&password=abc123456×tamp=1650961572897&nonceStr=TQbBR5qJO3rImsVJZ72rj5hTYmM6yxG675cba6dd6d4d75154624dbe9d770d451
utf-8转换后:
countryCode=86&userName=13618396959&password=abc123456×tamp=1650961572897&nonceStr=TQbBR5qJO3rImsVJZ72rj5hTYmM6yxG675cba6dd6d4d75154624dbe9d770d451
加密:
f6593a27bd2a8d594b3ce64858d41272
不对。。。。
累了,,,动态调试吧
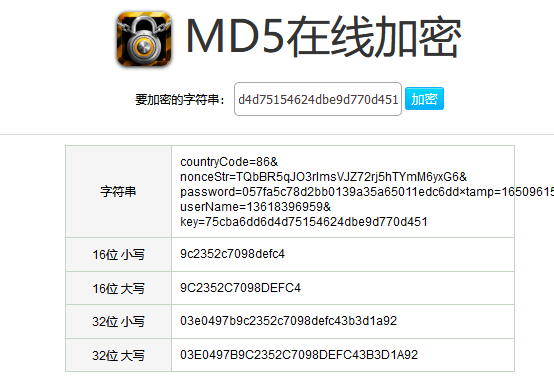
{“password”:”057fa5c78d2bb0139a35a65011edc6dd”,”countryCode”:”86”,”sign”:”03e0497b9c2352c7098defc43b3d1a92”,”userName”:”13618396959”,”nonceStr”:”TQbBR5qJO3rImsVJZ72rj5hTYmM6yxG6”,”timestamp”:”1650961572897”}
“countryCode=86&nonceStr=TQbBR5qJO3rImsVJZ72rj5hTYmM6yxG6&password=057fa5c78d2bb0139a35a65011edc6dd×tamp=1650961572897&userName=13618396959&key=75cba6dd6d4d75154624dbe9d770d451”
答案: 03e0497b9c2352c7098defc43b3d1a92
成功:
但是我还是不知道这个0为什么要填充
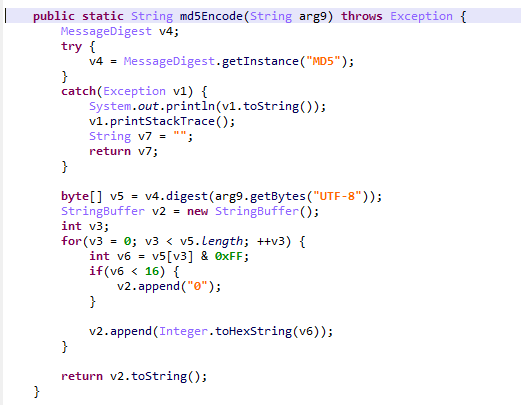
这一串实在没搞清楚是多少个0
标题叫断点调试,but,,,我并没有用到,,,
nonceStr
是随机的







